Best Google Dorking Tools in 2025 (Parser, Scraper, Searcher...)
Explore the best tools for automated Google dorking in 2025. Whether you call them scrapers, parsers, dorkers, or dork searchers, they all pull links from search engines like Google, Yahoo, Bing, and others, so we’ll simply refer to them as scrapers.

We’ll cover both paid and free options. Some focus purely on search scraping, while others cater to pentesting with extras like vulnerability scanning (XSS, SQL, ENV), dumpers, and more.

Googler is an open-source, command-line utility written in Python that mirrors much of Google’s search functionality. Key features include:
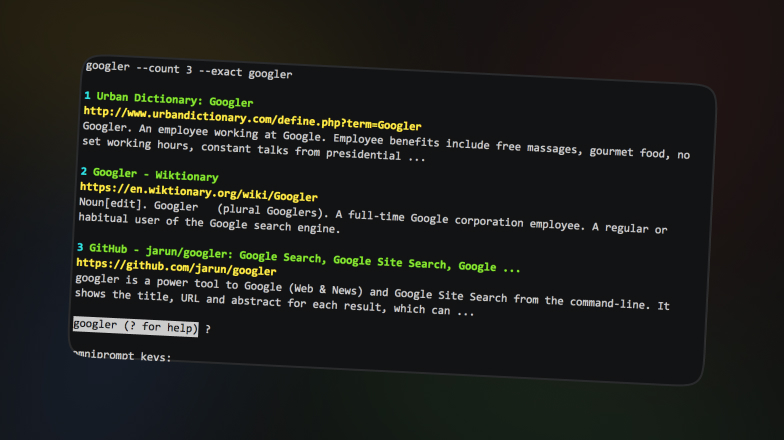
1. Prepare your dorks in a text file, for example dorks.txt
2. Run Googler in batch mode: googler --json --batch dorks.txt > results.json
3. Extract urls with JQ or a python script: jq -r ".[].link" results.json > links.txt
4. Post-processing: Feed links.txt into your crawler, vulnerability scanner, or data-analysis pipeline
AnalysisGoogler works, but it isn’t the strongest choice. It offers useful flags to shape results and output, yet it runs slowly, requires manual steps, and the outputs aren’t very friendly. You’ll also need to be comfortable with the CLI, and it’s not ideal for scraping hundreds of thousands of links.

DorkPlus is the go-to tool for pentesting and combolist dumping. It offers an advanced Google parser/scraper with very low bandwidth usage, plus an all-in-one suite: scraper, vulnerability scanner, dumper, dehasher, free dork generator, and other utilities.
1. Prepare your dorks (queries) in a text file, for example dorks.txt
2. Make a new task: select the engine (here Google), select your dork list, set the threads you want to use and select your proxies.
3. Save your results to a file: links.txt
4. Post-processing: Feed links.txt in their built-in Vulnerability Scanner.
AnalysisProsDorkPlus is the best tool out of the 3 in this article for multiple reasons: it's the fastest option, uses the least bandwidth, and has the smoothest GUI on the market.
It’s less modular than A-Parser, so you can’t target news or images or fully customize the scraper. It’s also a bit pricier than A-Parser.

A-Parser is a well-known all-in-one tool with a GUI instead of a CLI and supports a wide range of engines such as Google, Bing, and Yahoo. Notable features include:
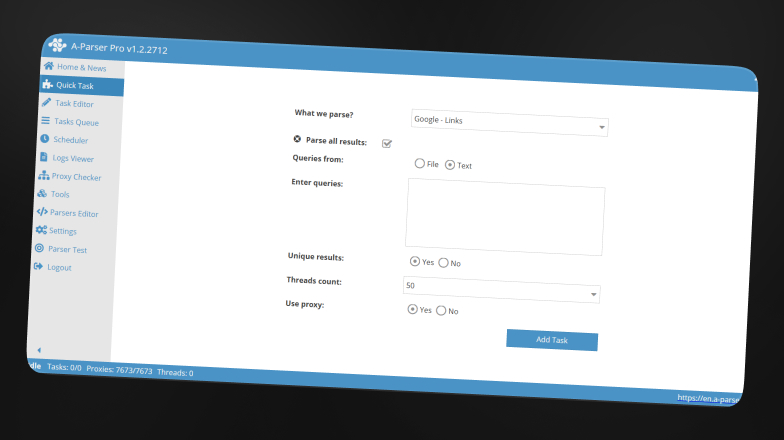
1. Prepare your dorks (queries) in a text file, for example dorks.txt
2. Make a new task: select the engine (here Google), paste your queries, set the threads you want to use and select your proxies.
3. Save your results to a file: links.txt
4. Post-processing: Feed links.txt into your crawler, vulnerability scanner, or data-analysis pipeline
AnalysisProsA-Parser is solid for shorter dork lists or specialized use cases like competitive research, SERP data, Google News, or targeted search engines. It’s advanced and has plenty of customization options for tailored results.
ConsThe depth of options can feel heavy if you want a simple load-and-go experience. It isn’t as fast as some competitors, and the overall process can feel resource-heavy.
The blog posts on this website are fictional and theoretical. They exist for educational purposes only and should never be treated as instructions to perform illegal or unauthorized activities.
The scenarios described are hypothetical and do not promote or encourage malicious or harmful actions. They reflect a professional penetration tester’s perspective, assuming proper permission and legal authorization to test a website, company, or network.
Our posts are not a call to action, and we do not condone illegal activity. Readers are responsible for complying with applicable laws and regulations.
By reading our posts, you acknowledge these terms. If you are not a professional or authorized individual, do not attempt to replicate any techniques described here.
Our content is for education only, and we strongly advise against using any information or techniques for malicious purposes.
Read next

Credential Stuffing and AntiPublic Checkers: What Security Professionals Need to Know

Google Dork Operators Cheat Sheet 2026: The Complete Guide

Is Google Dorking And SQLi Dead In 2026?

What Is An AntiPublic Checker And How Is It Used?

DorkPlus: The Ultimate Dork Scraper for Pentesting and Google Dorking

